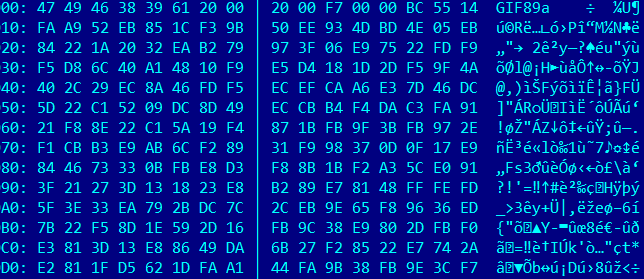
The criminals behind the malware delivery system for GameOver Zeus have a new trick. Encrypting their EXE file so that as it passes through your firewall, webfilters, network intrusion detection systems and any other defenses you may have in place, it is doing so as a non-executable “.ENC” file. If you are in charge of network security for your Enterprise, you may want to check your logs to see how many .ENC files have been downloaded recently.
Gary Warner wrote a blogpost over it, and shared some files and information with us. The question was, how the .enc file is decoded and used.
The droppers sent out through emails are pretty small, around 10-18 kb. These droppers have an obfuscation layer, so hard to directly analyze them. However, with volatility it was relatively easy with procexedump to extract a small, 5k downloader that actually connects to a server to download the related .enc file, decrypt and decompress it, and execute.
The encrypted files look like this at the beginning:
0000000000: 5A 5A 50 00 E7 31 0E 1E │ 02 17 0E 50 58 87 0E D1 ZZP ç1♫▲☻↨♫PX┼♫Ń
0000000010: 5C 87 3E AC A7 87 0E EB │ 58 BF 23 52 58 C7 0A 6B \┼>¬§┼♫ëXż#RXÇ◙k
0000000020: 41 87 E6 53 54 89 11 53 │ E2 89 0E E7 51 4A 2F EB A┼ćST%◄Sâ%♫çQJ/ë
0000000030: 58 86 42 9E 79 D3 66 3A │ 2B 87 2E 23 2A E8 69 21 X┼BžyÓf:+┼.#*či!
0000000040: 39 EA 0E 73 3B E6 60 3D │ 37 F3 2E 53 3A E2 2E 21 9ę♫s;ć`=7ó.S:â.!
ZZP\0 is a magic string, then a compressed and encrypted part is stored (here: 0xE7 0x31…)
After downloading the .enc file the dropper checks the magic:
.text:00971450 cmp byte ptr [esi], 5Ah
.text:00971453 jnz short loc_9714D2
.text:00971455 cmp byte ptr [esi+1], 5Ah
.text:00971459 jnz short loc_9714D2
.text:0097145B cmp byte ptr [esi+2], 50h
.text:0097145F jnz short loc_9714D2
.text:00971461 cmp [esi+3], bl
.text:00971464 jnz short loc_9714D2
.text:00971466 shl eax, 2
.text:00971469 push eax ; dwBytes
.text:0097146A push 8 ; dwFlags
… and does the decryption….
.text:0097149C loc_97149C: ; CODE XREF: start+455�j
.text:0097149C xor [esi+ecx*4], eax
.text:0097149F mov edi, [ebp+78h+Buffer]
.text:009714A2 inc ecx
.text:009714A3 shr edi, 2
.text:009714A6 cmp ecx, edi
.text:009714A8 jb short loc_97149C
eax stores the encryption key, which is 32 bits long.
The executable stores its configuration in a compressed form, but in cleartext.
0000001000: 85 B0 00 64 63 6D 73 73 │ 65 72 76 00 69 63 65 73 •° dcmsserv ices
0000001010: 2E 63 6F 6D 02 00 0C 00 │ 2F 69 6D 61 67 65 80 73 .com☻ ♀ /image?s
0000001020: 2F 73 74 6F 72 69 01 1C │ 08 6C 69 64 00 18 70 64 /stori☺∟◘lid ↑pd
0000001030: 66 2E 18 65 6E 63 0D B4 │ 0F 00 B8 37 B8 0A 1E 01 f.↑enc♪´☼ ¸7¸◙▲☺
0000001040: 0E 02 00 06 65 6C 65 63 │ 00 74 72 69 63 69 61 6E ♫☻ ♠elec trician
0000001050: 73 00 64 75 62 6C 69 6E │ 69 72 20 65 6C 61 6E 64 s dublinir eland
0000001060: 04 78 2F 77 00 70 2D 63 │ 6F 6E 74 65 6E 00 74 2F ♦x/w p-conten t/
0000001070: 75 70 6C 6F 61 64 00 73 │ 2F 32 30 31 34 2F 30 16 upload s/2014/0▬
0000001080: 31 22 70 02 6B 01 03 6B │ 00 00 00 00 00 00 00 00 1"p☻k☺♥k
The compression here is RtlDecompressBuffer standard windows call.
rtldecompressbuffer_dword_972000 = (int (__stdcall *)(_DWORD, _DWORD, _DWORD, _DWORD, _DWORD, _DWORD))GetProcAddress(v9, "RtlDecompressBuffer");
It is called like this:
rtldecompressbuffer_dword_972000(0x102u, v11, 1024, &unk_974000, 256, &v36);
0x102 stands for: 0x100 for max compression level, 0x02 for LZNT1 compression algorithm.
If you don’t have LZNT1 related code at hand, you might use the tool available at the following address: http://reboot.pro/files/file/121-lznt1-tools-bootmgrntfs/
It does not work for all the samples, but works most of the time.
So decompressed config looks like this:
0000000000: 64 63 6D 73 73 65 72 76 │ 69 63 65 73 2E 63 6F 6D dcmsservices.com
0000000010: 00 00 00 00 00 00 00 00 │ 00 00 00 00 00 00 00 00
0000000020: 2F 69 6D 61 67 65 73 2F │ 73 74 6F 72 69 65 73 2F /images/stories/
0000000030: 73 6C 69 64 65 73 2F 70 │ 64 66 2E 65 6E 63 00 00 slides/pdf.enc
0000000040: 00 00 00 00 00 00 00 00 │ 00 00 00 00 00 00 00 00
0000000050: 00 00 00 00 00 00 00 00 │ 00 00 00 00 00 00 00 00
0000000060: B8 37 B8 1E 00 00 00 00 │ 02 00 00 00 65 6C 65 63 ¸7¸▲ ☻ elec
0000000070: 74 72 69 63 69 61 6E 73 │ 64 75 62 6C 69 6E 69 72 triciansdublinir
0000000080: 65 6C 61 6E 64 2E 63 6F │ 6D 00 00 00 2F 77 70 2D eland.com /wp-
0000000090: 63 6F 6E 74 65 6E 74 2F │ 75 70 6C 6F 61 64 73 2F content/uploads/
00000000A0: 32 30 31 34 2F 30 31 2F │ 70 64 66 2E 65 6E 63 00 2014/01/pdf.enc
00000000B0: 00 00 00 00 00 00 00 00 │ 00 00 00 00 00 00 00 00
00000000C0: 00 00 00 00 00 00 00 00 │ 00 00 00 00 B8 37 B8 1E ¸7¸▲
00000000D0: 00 01 00 00 02 00 00 00 │ ☺ ☻
The 32-bits xor code used for encryption is stored 0x60 bytes after the beginning of this buffer, that means, for both servers it is 0b8 0x37 0xb8 0x1e.
This should be used cyclically on the .enc file to get the compressed file , which again is compressed with RTLCompressBuffer call.
So how to make a universal decoder for .enc files?
Let’s check this one:
0000000000: 5A 5A 50 00 5F 8D B8 53 │ E2 A7 B8 1D B8 37 B8 9C ZZP _Ť¸S⧸↔¸7¸ś
0000000010: BC 37 88 E1 47 37 B8 A6 │ B8 0F 95 1F B8 77 BC 26 Ľ7?áG7¸|¸☼•▼¸wĽ&
0000000020: A1 37 60 1E B4 39 A7 1E │ 02 39 B8 AA B1 FA 99 A6 ˇ7`▲´9§▲☻9¸Ş+út|
0000000030: B8 36 F4 D3 99 63 D0 77 │ CB 37 98 6E CA 58 DF 6C ¸6ôÓtcĐwË7?nĘXßl
I’m cheating and telling you that it will be decrypted to
0000000000: E7 BA 00 4D 5A 90 00 03 │ 00 00 00 82 04 00 30 FF çş MZ? ♥ '♦ 0˙
0000000010: FF 00 00 B8 00 38 2D 01 │ 00 40 04 38 19 00 D8 00 ˙ ¸ 8-☺ @♦8↓ Ř
0000000020: 0C 0E 1F 00 BA 0E 00 B4 │ 09 CD 21 B8 00 01 4C CD ♀♫▼ ş♫ ´○Í!¸ ☺LÍ
Where B8->00 53->4D E2->5A A7->90 is the transformation.
4D 5A is the standard PE header, and for all the .enc files, the next byte was 0x90. Before the MZ header, the compression magic always contains a 0x00 byte. So we have 4 fixed bytes. Hence let’s calculate the key:
1st byte: 0xB8 xor 0x00 = 0xb8
2nd byte: 0x53 xor 0x4D = 0x1E
3rd byte: 0xE2 xor 0x5A = 0xb8
4th byte: 0xA7 xor 0x90 = 0x37
Remember the config file? The key was B8 37 B8 1E, this is just a rotated version of it with 2 bytes shift as you know, the magic starts with two additional bytes.
So as these bytes are currerntly constants, it’s evident to create a generic decryptor too for the .enc files, that works without the hard coded key, only with the .enc files. After decrypting, of course, you have to run RTLDecompressBuffer to get the actual executable.
Note, there is another small encryption routine in the 5k dropper, we did not fully investigate what it codes:
.text:00971000 encrypt_sub_971000 proc near ; CODE XREF: start+4AF�p
.text:00971000
.text:00971000 arg_0 = dword ptr 4
.text:00971000 arg_4 = byte ptr 8
.text:00971000 arg_8 = dword ptr 0Ch
.text:00971000
.text:00971000 mov ecx, [esp+arg_8]
.text:00971004 test ecx, ecx
.text:00971006 jz short loc_971029
.text:00971008 movzx eax, [esp+arg_4]
.text:0097100D imul eax, 1010101h
.text:00971013 mov edx, ecx
.text:00971015 push ebx
.text:00971016 push edi
.text:00971017 mov edi, [esp+8+arg_0]
.text:0097101B shr ecx, 2
.text:0097101E rep stosd
.text:00971020 mov ecx, edx
.text:00971022 and ecx, 3
.text:00971025 rep stosb
.text:00971027 pop edi
.text:00971028 pop ebx
.text:00971029
.text:00971029 loc_971029: ; CODE XREF: encrypt_sub_971000+6�j
.text:00971029 mov eax, [esp+arg_0]
.text:0097102D retn
.text:0097102D encrypt_sub_971000 endp
(copied from cef76fa7b4b30f76c7b6d2eefa30d944 sample)